How it works
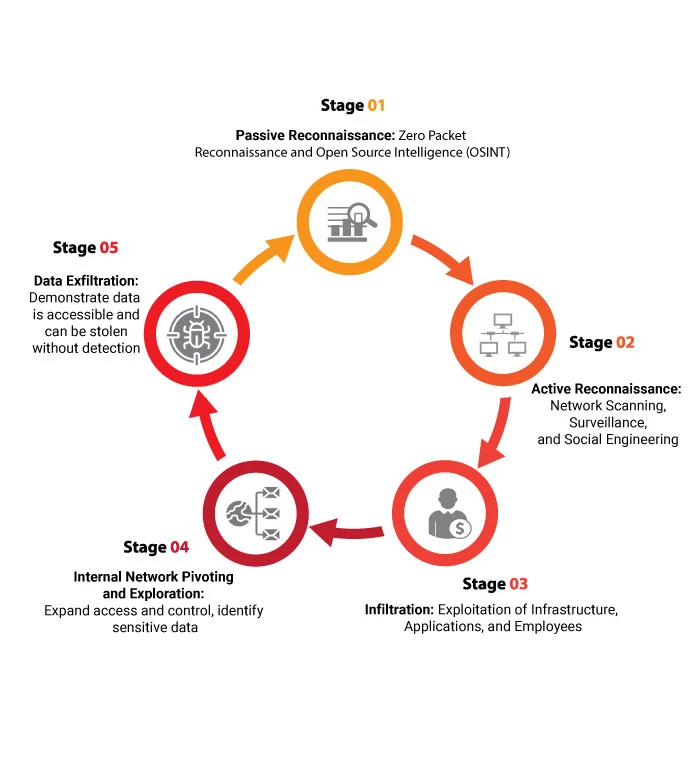
Multi-blended, adversarial-based attack simulation against people, software, hardware, and facilities performed simultaneously for the conservation of the target’s data security. If you need a full scale ‘no holds barred’ cyber attack launched at your organization or specific assets, Defmax’s Red Team assessments offer unparalleled insights into your security posture. Each Red Team engagement is unique and specifically tailored for every organization, but usually include the following scopes of work:
- Internal and External Network Penetration Testing
- Web, Mobile, and SaaS/Cloud Application Penetration Testing
- Social Engineering (Phishing, Vishing, Phone, In-Person)